Information security has been a hot topic and concern in recent years, with various hackers exploits regularly finding a spot in major headline news. As businesses have become more aware of the possibility of cyber exploitation, many have begun the process of educating themselves on good computer security practice.
By introducing more advanced firewall technologies, enforcing better password protection, and monitoring network security more acutely, businesses are falsely led to believe that they have all but eliminated the possibility of being targeted.
Contrary to common belief, hackers don’t really require direct access to a business internal network to begin exploiting their data. The reality is, many successful hackers approach their craft in a far less obvious way, by collecting discarded materials and equipment and slowly gathering the data they require to fully exploit the business operations. How do they do this? Below we’ll examine how old documents and technology are used to exploit a business, and how document destruction services can solve these problems.
1. Many Businesses Simply Throw Away Old Documents

As businesses accumulate paperwork and various other documents, they underestimate the quantity of exploitable data contained within. With time, many documents are no longer needed, and as such are simply thrown away. Although this may seem logical, this is a particularly concerning practice where confidential and valuable data is concerned.
Employees and even managers often make the critical mistake of writing down vital information, such as login passwords, rather than commit them to memory. If just one of these logins was to eventually be discarded, it could be exploited in order to gain direct access to a business network, from which a great deal of valuable data could be extracted.
While this approach to exploitation is old fashioned, it is still effective to this day. Many businesses have begun shredding their documents personally in and attempt to solve this issue, however.
2. Poorly Shredded Documents are Just as Valuable as Non-Shredded Documents

Though shredding documents is good security practice, the fact of the matter is that most businesses that personally attempt to shred their own obsolete paperwork do a poor job of it. Documents which are simply run through a common shredder a single time and then thrown away still pose a security risk. A sufficiently motivated criminal entity has no issues with piecing together bits and pieces of information in order to capitalize on it in the future.
3. Going Digital Isn’t a True Solution

In order to combat the vulnerabilities of paperwork, many businesses have adopted an entirely digital model. All paperwork is managed digitally, so no paper documents ever reach the trash. Unfortunately, digital too can be exploited by more simple means than how hard-drive technology works. Keeping with the garbage searching, hackers often seek discarded computer equipment, specifically hard-drives, in order to retrieve data from them.
Most users don’t have a solid grasp on how hard-drive technology works, and underestimate how easy it is to recover data from them, in spite of any efforts to wipe the drive clean of data. The solution to this concern is surprisingly simple in theory, and that is to destroy any obsolete hard-drives.
4. Completely Destroying Drives isn’t Easy
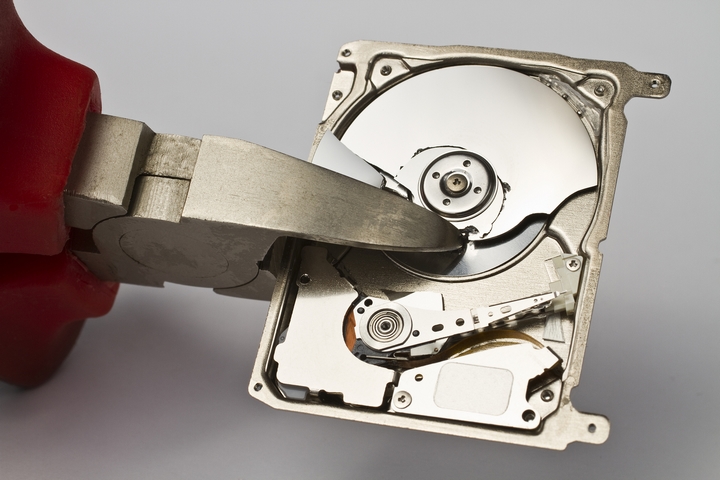
Destroying a hard-drive removes any possibility of data being recovered, however, the task is much easier said than done. In order to ensure that a drive cannot be recovered, it must be totally destroyed. Simply breaking it into a few pieces isn’t enough.
This is where the professionals come in. Professional data destruction and shredding services can guarantee the complete destruction of any drives or documents. This guarantee is achieved by running old drives and documents through industrial, high powered destruction equipment, which eliminates entirely the possibility of discarded data being exploited by hackers.
So the next time your business is throwing away old documents and equipment, consider the security risks involved. Rather than take an unnecessary risk, call a professional and dispose of your data the safe way. Only then can you be sure that your data is secure.